Incident halted. Response accelerated.
Block lateral movement, detect and isolate compromised users, and accelerate recovery in Active Directory environments under attack – because in an incident, every second counts. It’s like having a firewall on your domain controllers.
The missing piece in your IR toolkit.
Silverfort integrates seamlessly with IAM systems so you can start the response process by pinpointing and containing compromised accounts. Stop attackers in their tracks, freeze malicious activity and investigate the incident with real-time, actionable telemetry—without killing productivity.
Instant containment
Flip the script on identity response by instantly isolating malicious presence with MFA and Authentication Firewall policies on all users and resources. Block the attack from spreading with a single click.
Effortless detection
Let attackers reveal their presence through denied access attempts or blocked MFA challenges. Investigate without disturbing business operations and trace the attacker’s movements back to patient zero.
Rapid deployment
Get identity-first incident response within hours of deploying our platform – even in the most complex multi-domain environments with hundreds of Domain Controllers.
The Silverfort Identity Security Platform
How it works
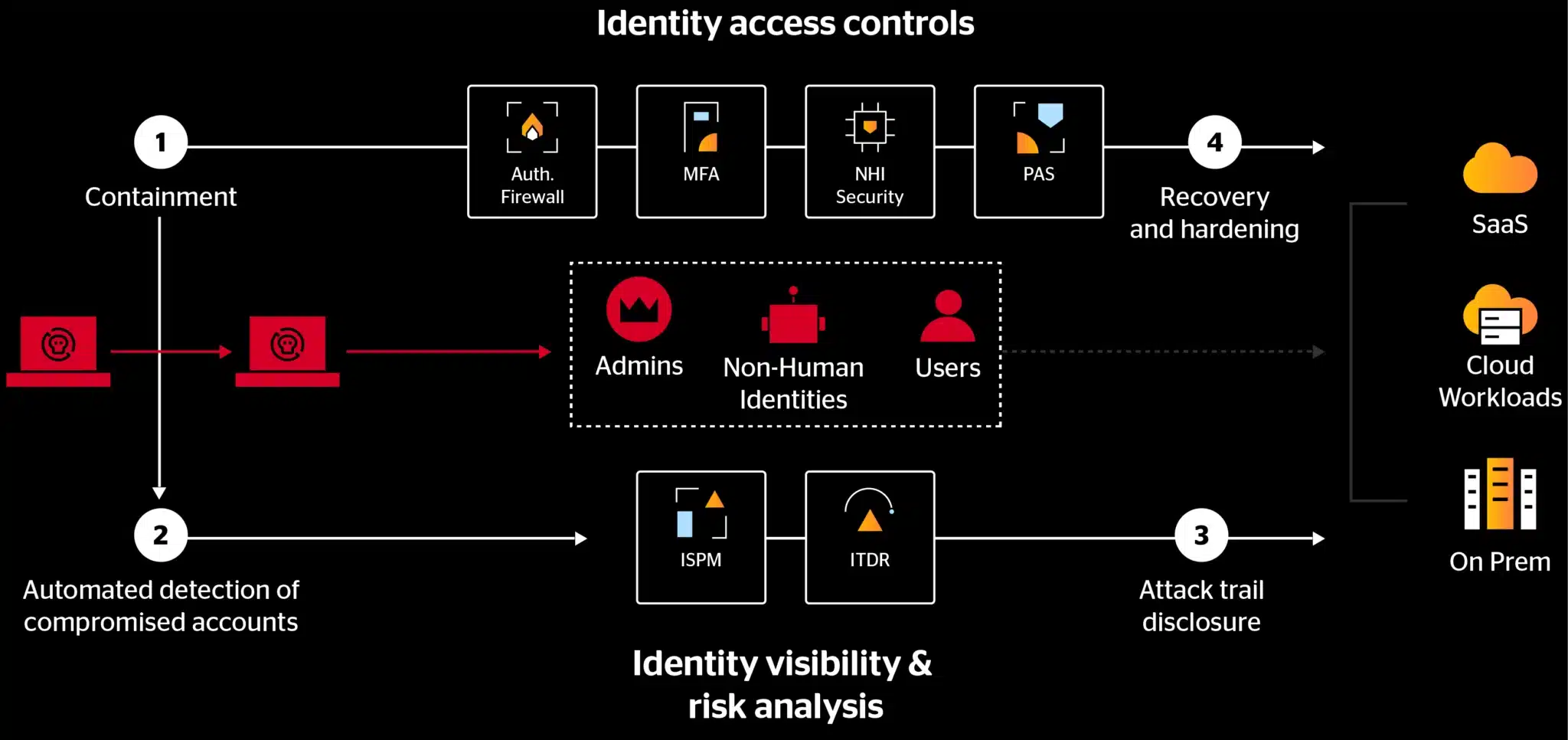
Start your IR process with identity.
Lock down without killing productivity
Take action immediately by leveraging the combined power of MFA and Authentication Firewall to stop an attack in its tracks, regardless of lateral movement TTPs or tools. Eliminate the need for lengthy investigations by containing the attack before compromised accounts have been identified.
Easily identify compromised accounts
Use denied MFA and blocked access attempts to hone in on compromised accounts. Our detailed audit trail can help you trace the attacker’s path back to patient zero, so you can focus your forensic efforts on the affected endpoints.
Recover and remediate at your own pace
Maintain critical security measures while you restore user access and mitigate any identity-related security weaknesses exploited during the attack, such as shadow admins, unmonitored service accounts, and unconstrained delegation.

Fortifying identity protection:
The Silverfort Identity IR Playbook
While there’s an established IR playbook to handle the malware and network aspects of cyberattacks, the identity aspect is lacking. There are no common procedures to identify compromised user accounts and prevent attackers from using them to spread within the targeted environment rapidly and efficiently. Our Identity IR playbook fills this gap, combining real-world solutions and tactics with the experiences of multiple customers who have used it to expedite and optimize their IR processes.
Step-by-step playbook for IR success
From containment to recovery, we cover it all.
Zoom in to service accounts and NHIs
Get unique insights into your NHIs and how to tackle them in an incident.
Flip the script on IR
Don't wait for too late. Start the IR process with a complete malicious access lockdown.

We dared to push identity security further.
Discover what’s possible.
Set up a demo to see the Silverfort Identity Security Platform in action.