
Silverfort Named a Gartner Cool Vendor in Identity and Access Management

By Dana Tamir, VP Market Strategy, Silverfort


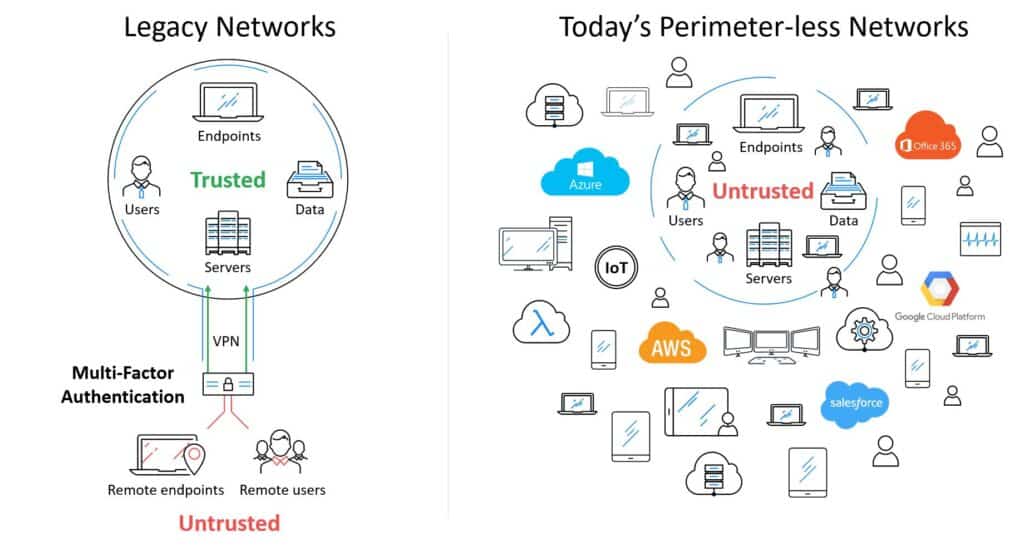
Gartner has just named Silverfort a “Cool Vendor” in Identity and Access Management (IAM). Needless to say, we are thrilled and very honored to receive such recognition. Gartner’s report explains that “Digital businesses must achieve a great user experience, and support digital transformation and optimization as well as the shift of workloads to the cloud.” We completely agree. Corporate networks are going through dramatic changes in recent years, due to IT revolutions such as the cloud, Internet of Things (IoT), Bring Your Own Device (BYOD) and more. In this new reality, with countless devices and services that are all connected to each other without clear perimeters, traditional authentication solutions become irrelevant, and a new approach is needed.
What’s So Cool About Silverfort?
We attribute Silverfort’s rise as a Next-Generation Authentication vendor to the following factors:
- It’s agentless: Yes, that’s true! Silverfort can enforce secure access to any system, no matter where it is, or what it is, without installing software agents on it and without requiring code changes. This means that it’s not only simple to deploy, but it also automatically protects new assets or shadow IT systems without having to integrate with them one by one.
- It doesn’t require proxies and doesn’t need to decrypt network traffic: Silverfort is not deployed as a proxy between the users and the applications or resources they are accessing. That’s because proxies assume there is some perimeter where they can monitor user access. In today’s enterprises, where so many connected users, devices and systems, on-premises and in the cloud, perimeters dissolve and deploying proxies becomes impossible. We believe that this is a major barrier: Where will you deploy a proxy to capture all user-to-machine and machine-to-machine interactions across the different environment, and within each environment? Silverfort’s innovative architecture removes the need to answer this difficult question. To do that, we had to overcome another challenge that was thought to be impossible – analyzing encrypted authentication protocols without decrypting the traffic.
- It can secure authentication and access to any sensitive system, including those considered ‘unprotectable’ until today: By eliminating the need for agents, proxies or code changes, Silverfort can enable secure authentication (including MFA and adaptive authentication) for any system. This includes systems that could not be protected until today, like homegrown and legacy applications, critical IT infrastructure (hypervisors, DCs), IoT devices, SCADA servers, healthcare systems like PACS and EHR, dynamic IaaS environments, PCI servers, databases, file shares and more.
- It enables enterprises to achieve Zero Trust security without rebuilding their networks: As traditional network perimeters dissolve, identity and access management is becoming the new perimeter. More and more organizations look to Zero Trust as a solution, because they can no longer assume internal users are trusted. However, implementing a Zero Trust architecture usually requires companies to rebuild their network. Silverfort’s agentless and proxyless architecture is the first to enable identity-based Zero Trust security without this need, making it simple and achievable for any enterprise.
- It leverages an AI-Driven Risk Engine to continuously analyze risk and trust: Due to the holistic nature of Silverfort’s architecture, it continuously monitors all the access activities of all users and systems, analyzing 20x-50x more access activity than any other authentication solution. To continuously analyze all access activity, as well as external threat indicators provided by other security solutions, Silverfort leverages a first-of-its-kind AI-Driven Risk Engine. Silverfort’s Risk Engine continuously profiles and analyzes user behaviors using machine learning and reinforcement learning to apply the most accurate MFA and access policies.
- It can detect and block threats in real-time: Silverfort’s AI-Driven Risk Engine can detect a wide range of threats in real time, including behavior anomalies as well as known malicious patterns like brute-force attacks, lateral movement (e.g. Pass the Hash), ransomware and more. Using adaptive policies, it can block access or require users to authenticate with a 2nd factor before allowing them to continue with high-risk access. Silverfort step-up authentication can also be triggered by external threat indicators sent by other security products (including Palo Alto Networks, Check Point, Microsoft and others). So, if your firewall detected a suspicious user or device, Silverfort can now step-up the authentication for any attempt to access any system, even when coming from inside the perimeter.
- It lets organizations maximize security while minimizing disruptions: Today, organizations are struggling to deal with the high number of false-positive alerts. Blocking users because of false positive alerts is very disruptive and puts a lot of pressure on the SOC and helpdesk, but at the same time it’s crucial to block actual threats. Silverfort enables organizations to step-up the authentication requirements in response to real-time threats and allow access only to verified users. This dramatically reduces overhead for the SOC and helpdesk. So, the result is better response with less disruptions to your users and business.
We can continue listing more benefits and advantages, but why don’t you see for yourself? Contact us today to schedule a demo – we would love to show you more.

Dana Tamir, VP Market Strategy, Silverfort
Dana is a veteran of the cybersecurity industry with over 15 years of real-world expertise and leadership roles in leading security companies. Prior to Silverfort, Dana served as VP Marketing at Indegy. Before that, she served as Director of Enterprise Security at Trusteer (acquired by IBM in 2012). She also held various roles at Imperva, Symantec, Bindview, and Amdocs. Dana holds an engineering degree from the Technion – Israel Institute of Technology, in addition to a number of industry and vendor certifications.
To learn more about Silverfort and see a demo, contact us today!
